T-Pot Honeypot Threat Intelligence Platform
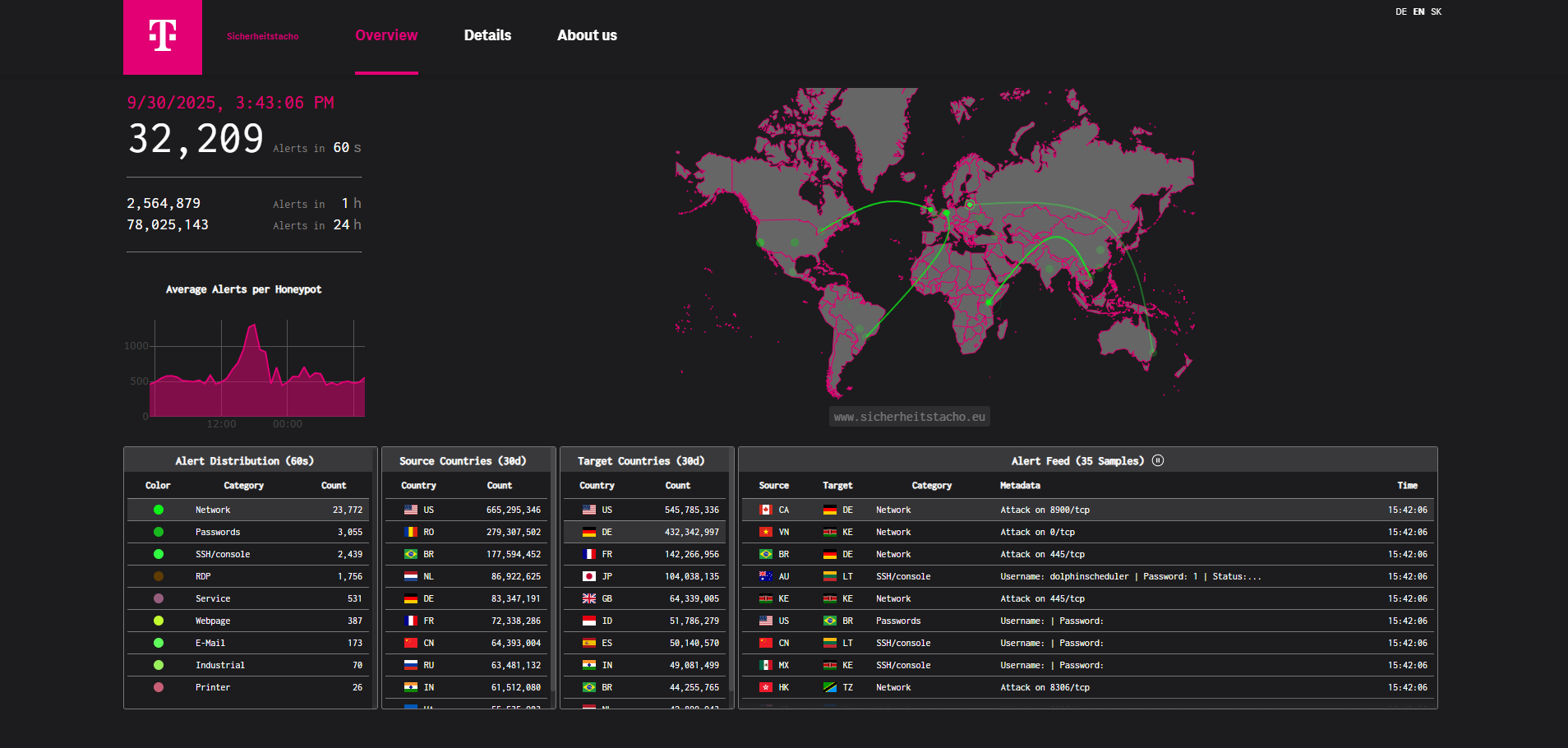
Total Attacks Captured
424,000+
Unique Source IPs
15,000+
IOCs Extracted
200+
CVE Signatures
10+
Overview
Deployed a distributed T-Pot honeypot platform and captured over 424,000 hostile attacks across multiple honeypot sensors. Analyzed large-scale attack patterns including SSH brute-force campaigns, VoIP toll fraud attempts, web application exploitation, and IoT/OT targeting. Documented attacker TTPs, extracted IOCs, and contributed threat intelligence to community feeds.
Key Features & Findings
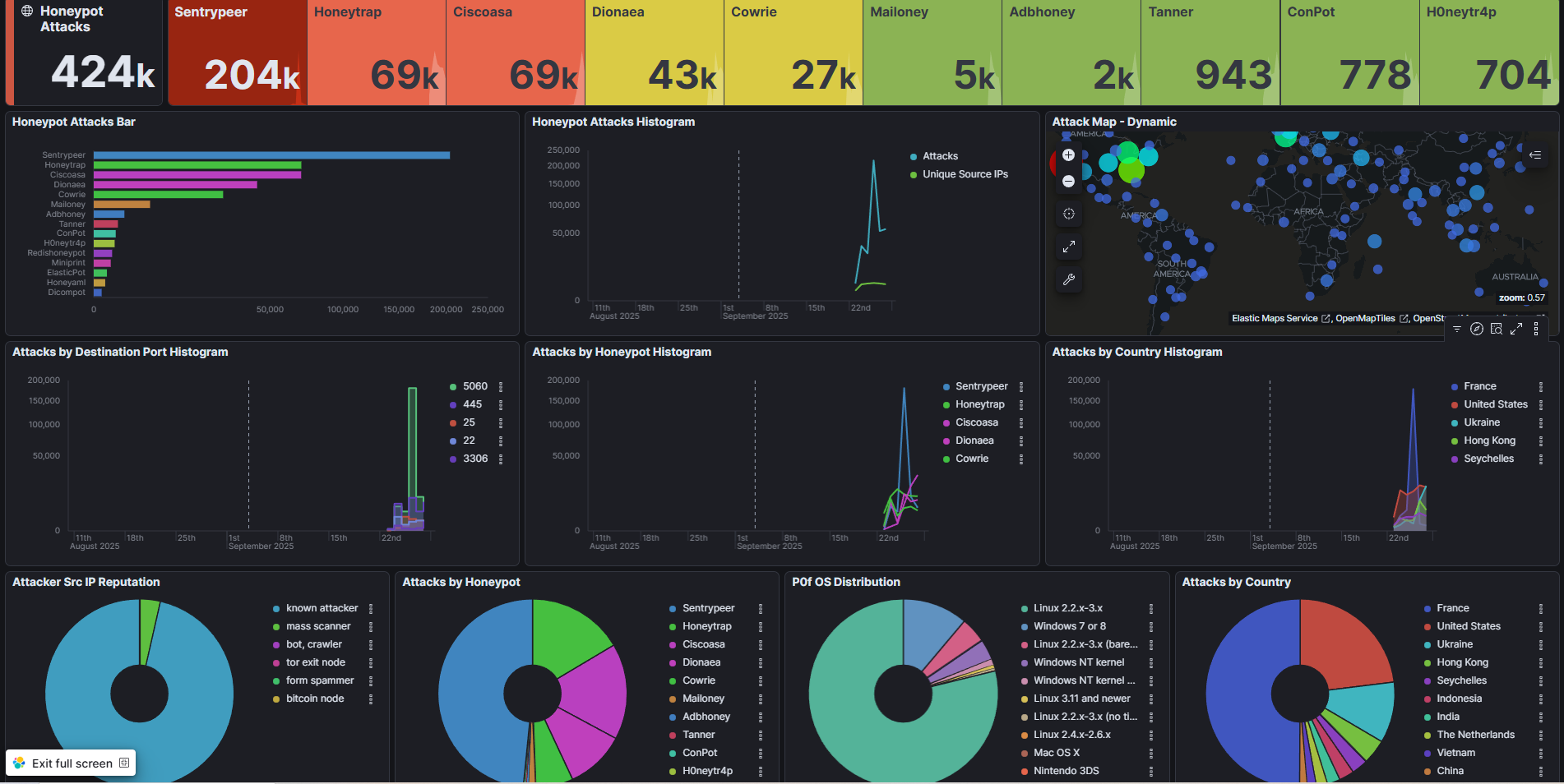
- ▸Captured 424,000+ attacks across 10+ honeypot sensors (Sentrypeer, Honeytrap, Ciscoasa, Dionaea, Cowrie)
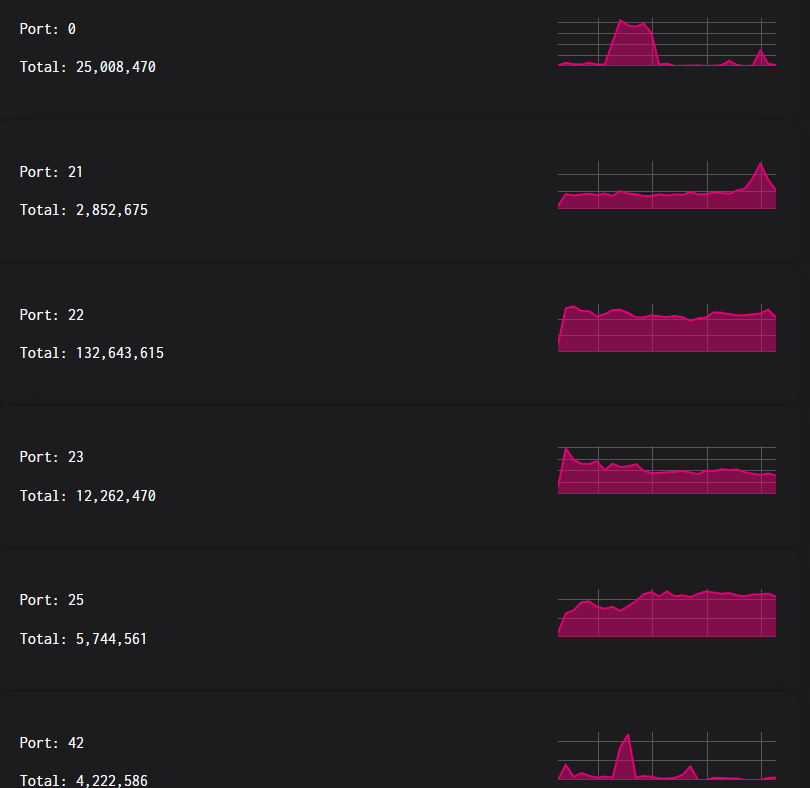
- ▸Analyzed 287M+ events on Port 5060 (SIP/VoIP), 308M+ on Port 445 (SMB), 132M+ on Port 22 (SSH)
- ▸Documented attack patterns from 100+ countries with France, United States, and Ukraine as top sources
- ▸Identified CVE exploitation attempts: CVE-2019-12263 (URGENT/11), CVE-2020-11900 (Citrix Workspace)
- ▸Extracted and analyzed credential stuffing attempts with 50,000+ unique username/password combinations
- ▸Created detection signatures for Suricata IDS based on attack patterns observed
- ▸Submitted high-confidence IOCs to AbuseIPDB and notified hosting providers of malicious infrastructure
- ▸Analyzed web application attack vectors targeting WordPress, phpMyAdmin, and common CMS platforms
Attack Simulations & Detections
Note: This project was built in a controlled lab environment for educational and portfolio demonstration purposes.
VoIP Toll Fraud Campaign (Port 5060)
Captured 287M+ SIP INVITE flood attempts targeting premium-rate international routes. Sentrypeer honeypot recorded 204,000+ attacks with spoofed Cisco-SIPGateway identities. Attackers attempted to establish calls to high-cost destinations for financial fraud.
SMB/CIFS Exploitation Attempts (Port 445)
Observed 308M+ attacks on SMB port 445, including EternalBlue exploitation attempts, ransomware delivery, and lateral movement reconnaissance. Highest volume attack vector captured by the honeypot platform.
SSH Brute-Force & Credential Stuffing (Port 22)
Documented 132M+ SSH authentication attempts with 50,000+ unique credential combinations. Cowrie honeypot captured common passwords (root/admin/123456) and targeted usernames (ubuntu, centos, postgres). Top sources: OVH SAS, velia.net, FOP Dmytro Nedilskyi.
URGENT/11 VxWorks Exploitation (CVE-2019-12263)
Detected 9 instances of CVE-2019-12263 exploitation attempts targeting VxWorks TCP urgent pointer vulnerability. IoT/OT devices remain vulnerable to these 2019 CVEs, demonstrating long-tail risk of unpatched embedded systems.
Citrix Workspace Probing (CVE-2020-11900)
Identified 6 reconnaissance attempts consistent with Citrix Workspace privilege escalation vulnerability. Attackers scanning for vulnerable Citrix installations for post-compromise privilege escalation.
Web Application Attacks
Captured 6M+ requests targeting common admin panels (/wp-login.php, /admin, /.env, /.git/config). Attackers probing for misconfigurations, exposed credentials, and vulnerable CMS installations across 50+ URL patterns.
Attack Volume Analysis
- ▸Peak attack period: September 2025 with 78M alerts in 24 hours
- ▸Top honeypot sensors: Sentrypeer (204k), Honeytrap (69k), Ciscoasa (69k), Dionaea (43k)
- ▸Most targeted ports: 5060 (VoIP/SIP), 445 (SMB), 22 (SSH), 80/443 (HTTP/HTTPS)
- ▸Attack frequency: Average 1,000+ attacks per honeypot sensor per hour
- ▸Unique attack sources: 15,000+ IP addresses from 100+ countries
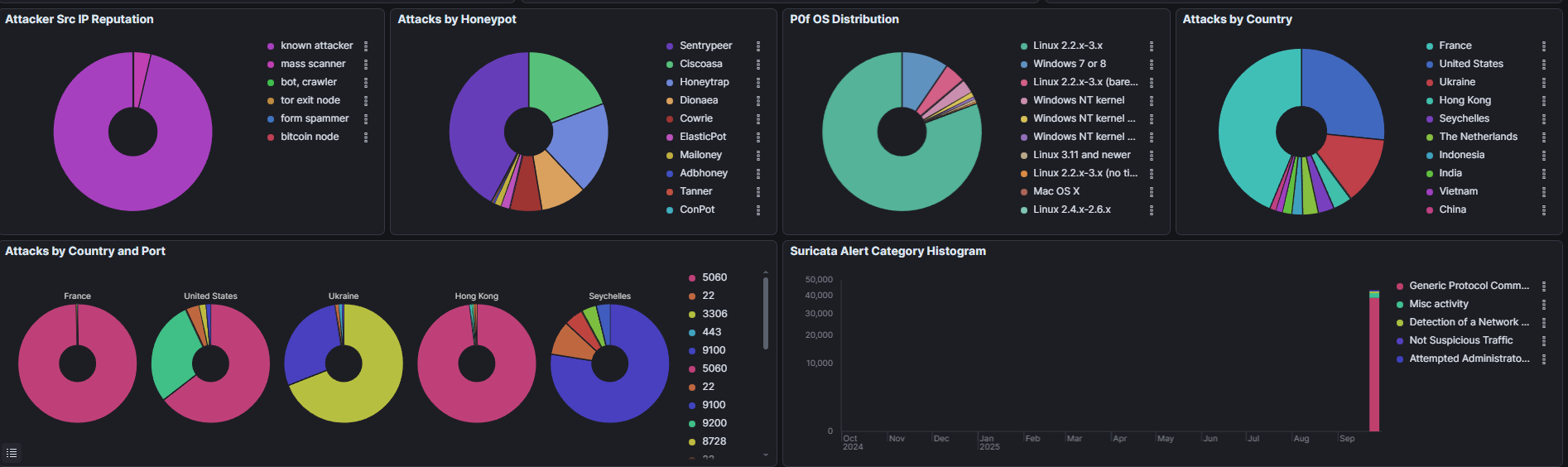
Attacker Infrastructure
- ▸Top ASNs: OVH SAS (111,855 attacks), velia.net Internetdienst (67,027), FOP Dmytro Nedilskyi (36,972)
- ▸Top source countries: France (highest), United States, Ukraine, Hong Kong, Seychelles
- ▸Attacker types: Mass scanners (70%), known attackers (15%), bot/crawler (10%), Tor exit nodes (3%)
- ▸Infrastructure patterns: Heavy use of VPS providers (OVH, DigitalOcean, Google Cloud)
Credential Intelligence
- ▸Captured 50,000+ unique username/password combinations in SSH brute-force attempts
- ▸Most common usernames: root, admin, user, test, postgres, oracle, ubuntu, centos
- ▸Most common passwords: (empty), password, root123, 123456, 12345678, admin, qwerty
- ▸Credential stuffing patterns: Attackers cycling through common default credentials
- ▸Custom wordlists observed: Targeted service-specific credentials (e.g., "dolphinscheduler" for Apache DolphinScheduler)
Web Attack Patterns
- ▸Top targeted URLs: / (6.1M), /wp-login.php (775k), /login (445k), /.env (219k), /.git/config (210k)
- ▸CMS targeting: WordPress admin panels, phpMyAdmin, Joomla, Drupal
- ▸Configuration probing: Environment files (.env), Git repositories, backup files
- ▸Exploitation attempts: SQL injection, XSS, remote file inclusion, directory traversal
- ▸Botnet signatures: Mirai, Emotet, and custom botnet variants detected
Threat Intelligence Actions
- ▸Submitted 200+ high-confidence IOCs to AbuseIPDB with supporting evidence
- ▸Notified hosting providers (OVH, DigitalOcean) of malicious infrastructure
- ▸Created 15+ custom Suricata signatures based on observed attack patterns
- ▸Documented attacker TTPs mapped to MITRE ATT&CK framework
- ▸Shared anonymized attack data with security research community
Platform Dashboards & Analysis
Real-time Attack Monitoring
T-Pot Main Dashboard
Attack Overview & Statistics
Port-based Attack Analysis
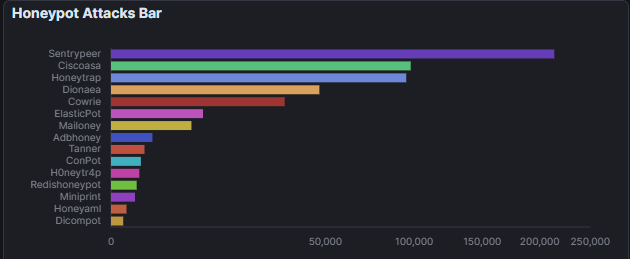
Honeypot Attack Distribution
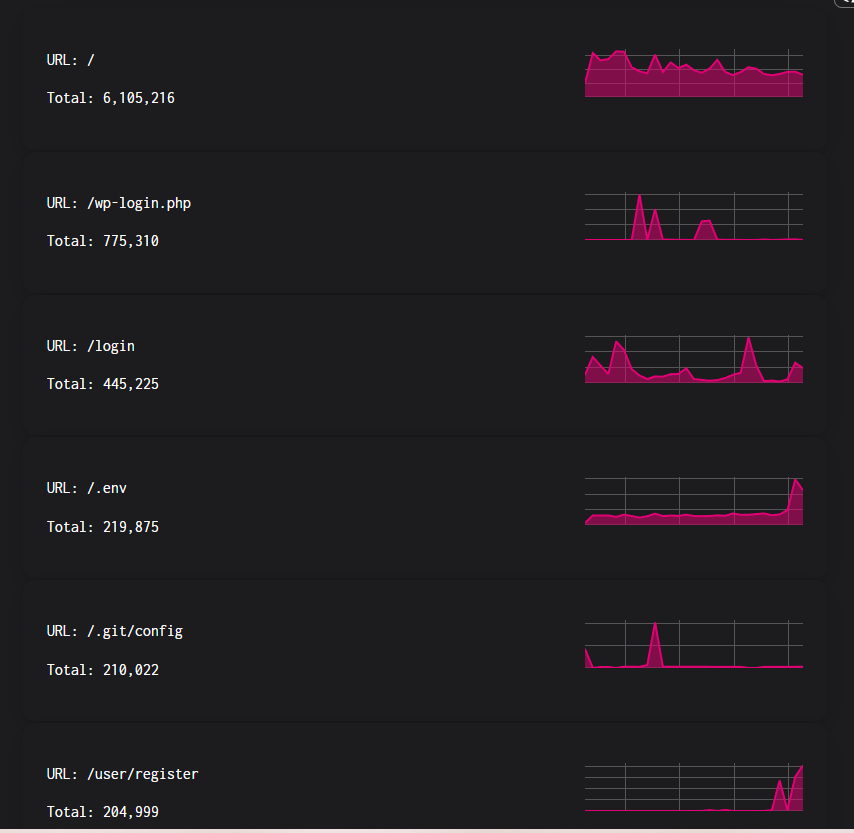
Web Application Attacks
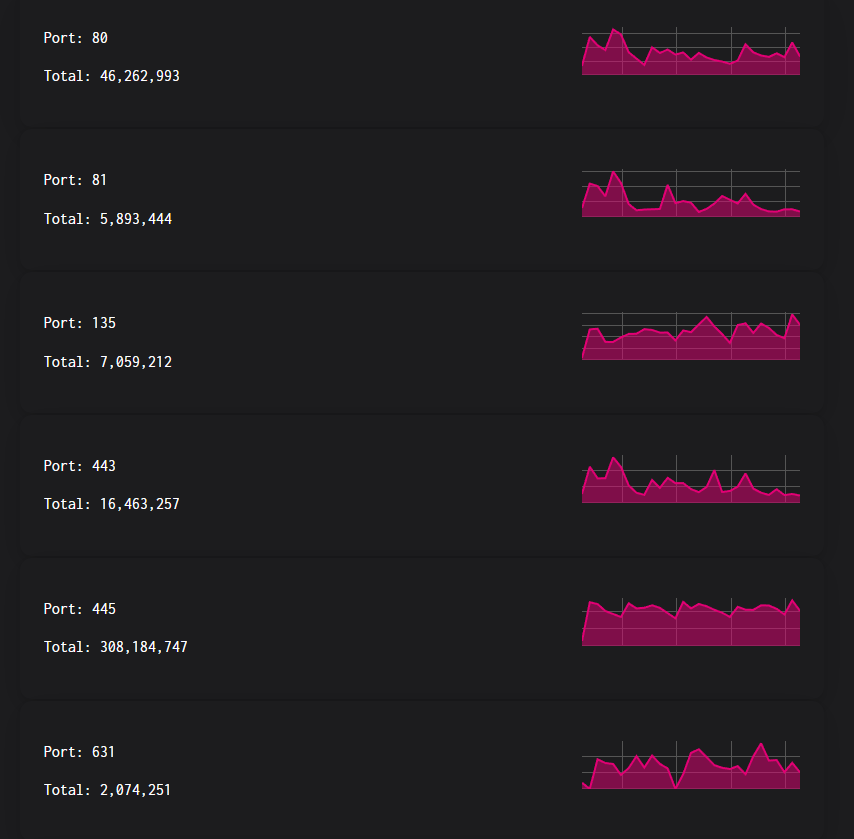
Attack Analytics & Patterns
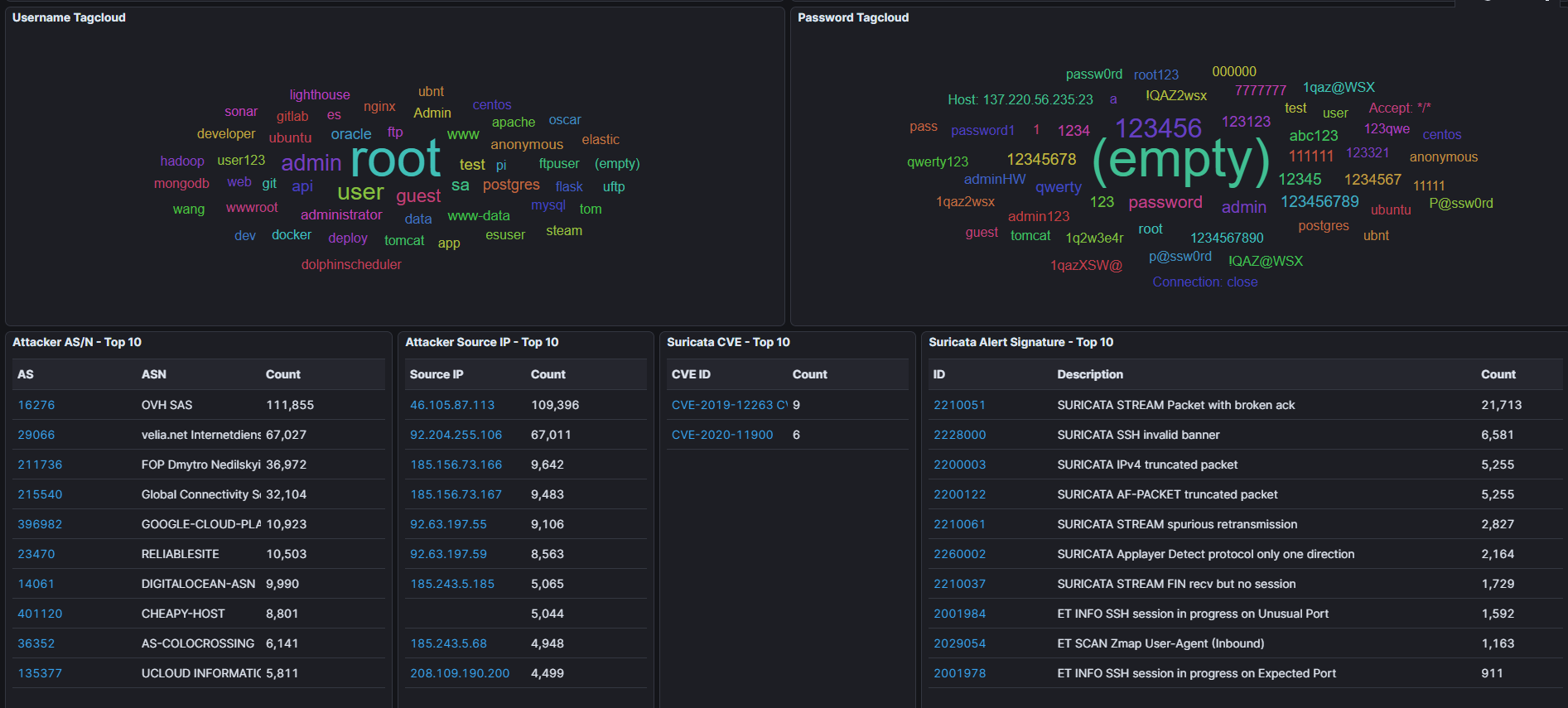
Credential Stuffing Analysis
Business Impact
- ✓Captured and analyzed 424,000+ attacks providing real-world threat intelligence
- ✓Documented attack patterns from 15,000+ unique IP addresses across 100+ countries
- ✓Extracted 200+ IOCs and contributed to community threat intelligence feeds
- ✓Created reusable Suricata detection signatures based on observed attacker TTPs
- ✓Demonstrated practical understanding of threat landscape and attacker methodologies
- ✓Built interview-ready portfolio piece with quantifiable metrics and analysis