AI-Powered SOC Automation Platform
Detection Rules
10
Alert Triage Time
<2 min
Attack Scenarios
9+
MITRE ATT&CK Tactics
6
Overview
Built an end-to-end Security Operations Center (SOC) automation platform in a controlled lab environment that detects, analyzes, and responds to security threats using AI-powered intelligence enrichment. Successfully simulated real-world attacks and demonstrated automated threat detection across 10+ attack vectors mapped to MITRE ATT&CK framework. The platform reduces estimated alert triage time from 15 minutes to under 2 minutes through intelligent automation.
Key Features & Findings
- ▸Created 10 production-ready detection rules covering credential dumping, process injection, PowerShell abuse, and brute-force attacks
- ▸Integrated GPT-4 for automated threat analysis with natural language intelligence summaries and MITRE ATT&CK mapping
- ▸Automated IOC enrichment using VirusTotal (file hash reputation) and AbuseIPDB (IP reputation scoring)
- ▸Deployed Sysmon with SwiftOnSecurity configuration for enhanced endpoint visibility (15+ event types)
- ▸Validated detection capabilities using real attack tools: Metasploit, Meterpreter, Hydra for RDP brute-force
- ▸Real-time Slack notifications with comprehensive alert details and remediation recommendations
- ▸N8N workflow automation orchestrating data flow from Splunk → AI Analysis → Threat Intel → Slack
- ▸Successfully detected 9/10 simulated attack scenarios with minimal false positives
Platform Screenshots
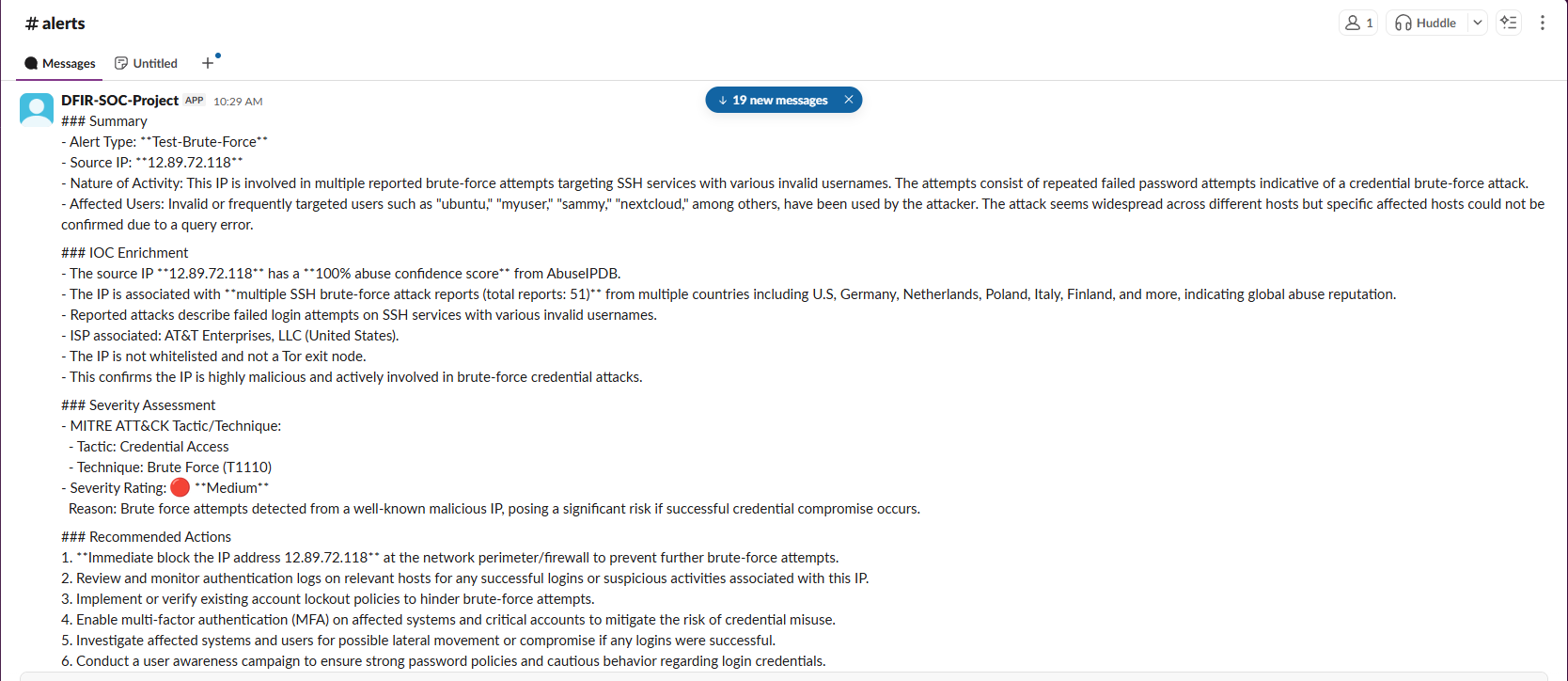
AI-Powered Brute Force Alert
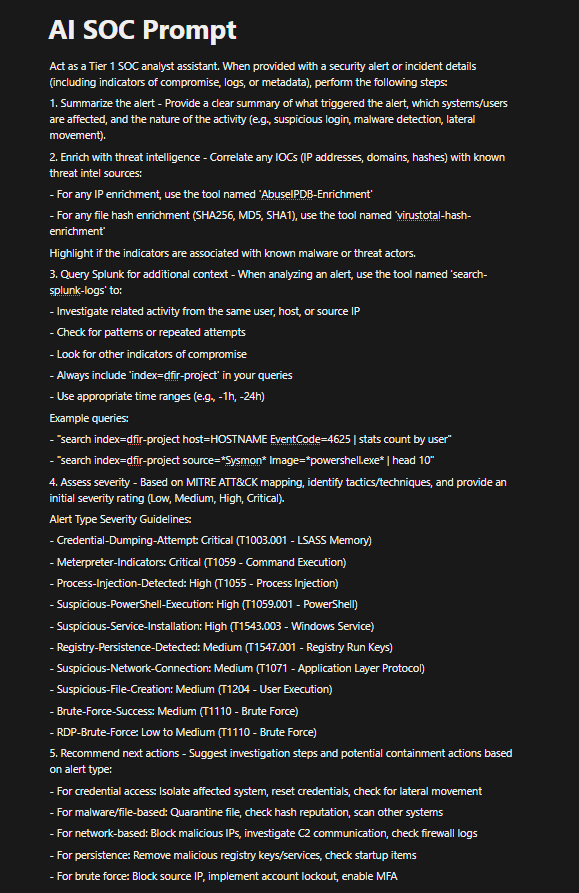
AI SOC Analyst Prompt
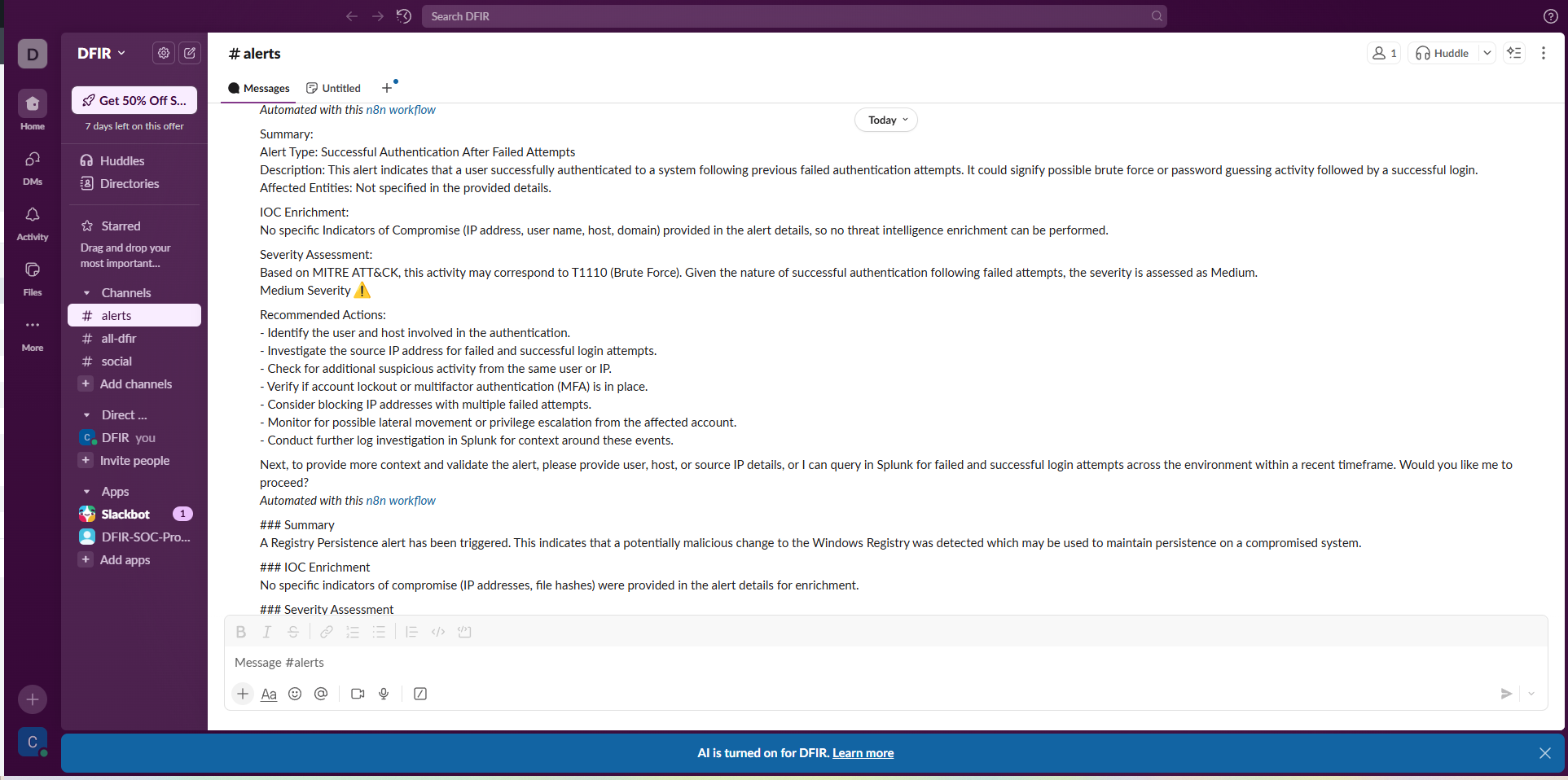
Multiple Security Alerts
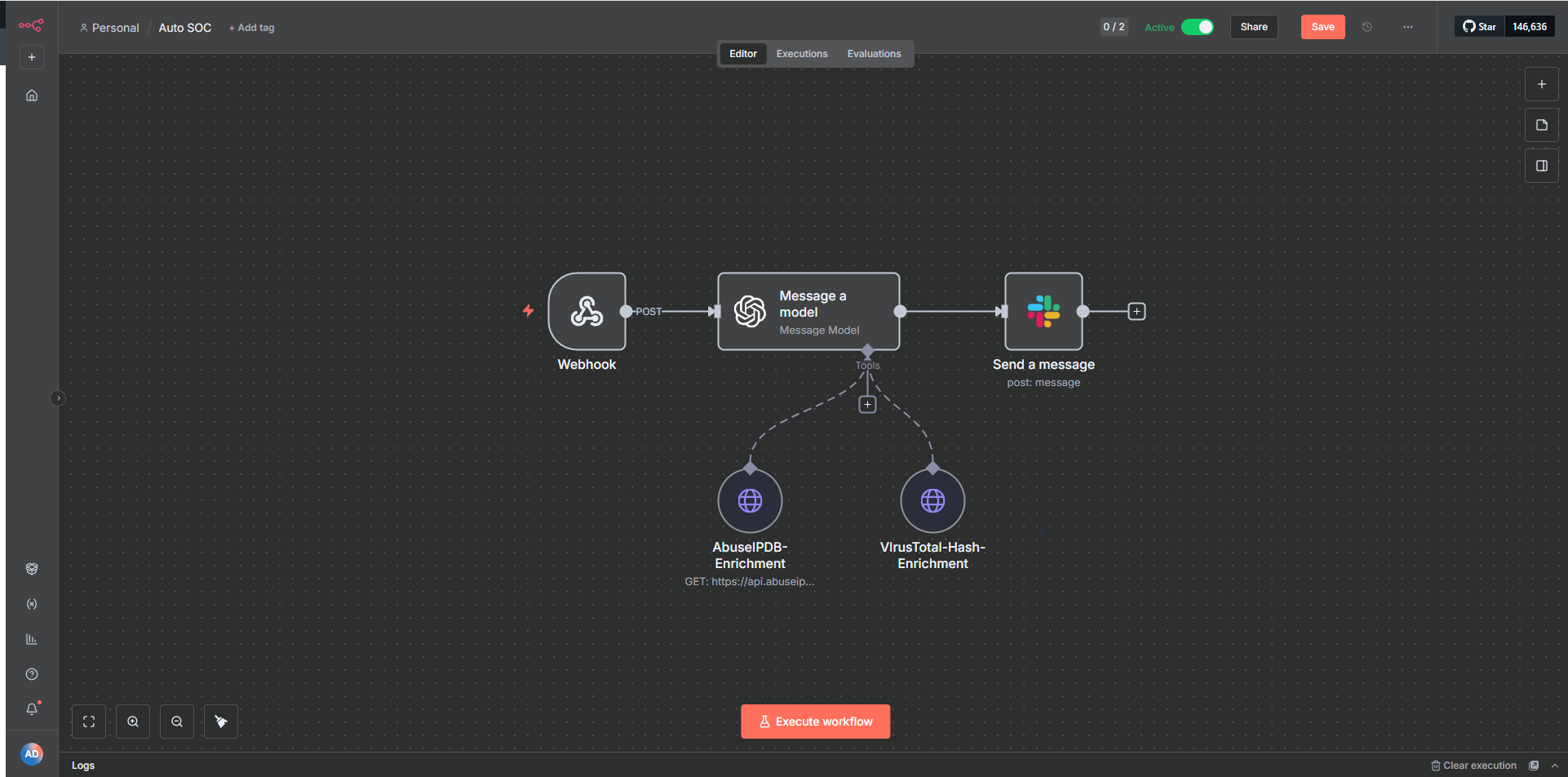
N8N Automation Workflow
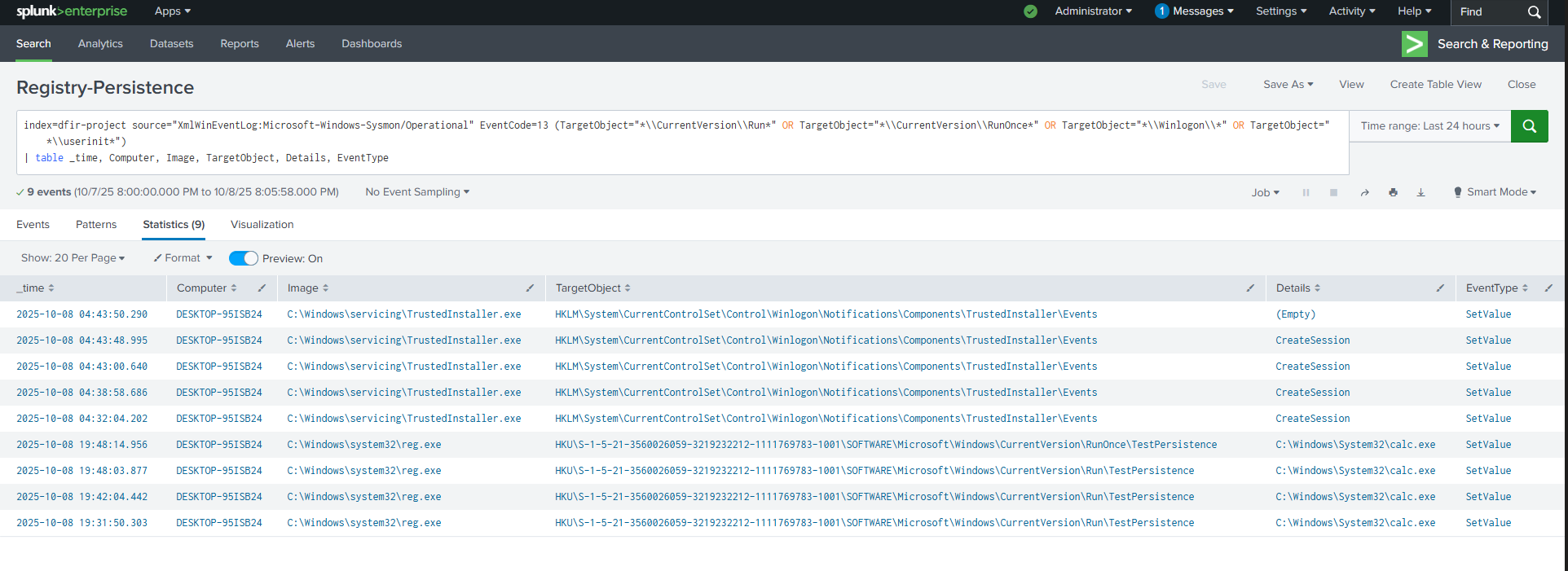
Splunk Registry Persistence Query
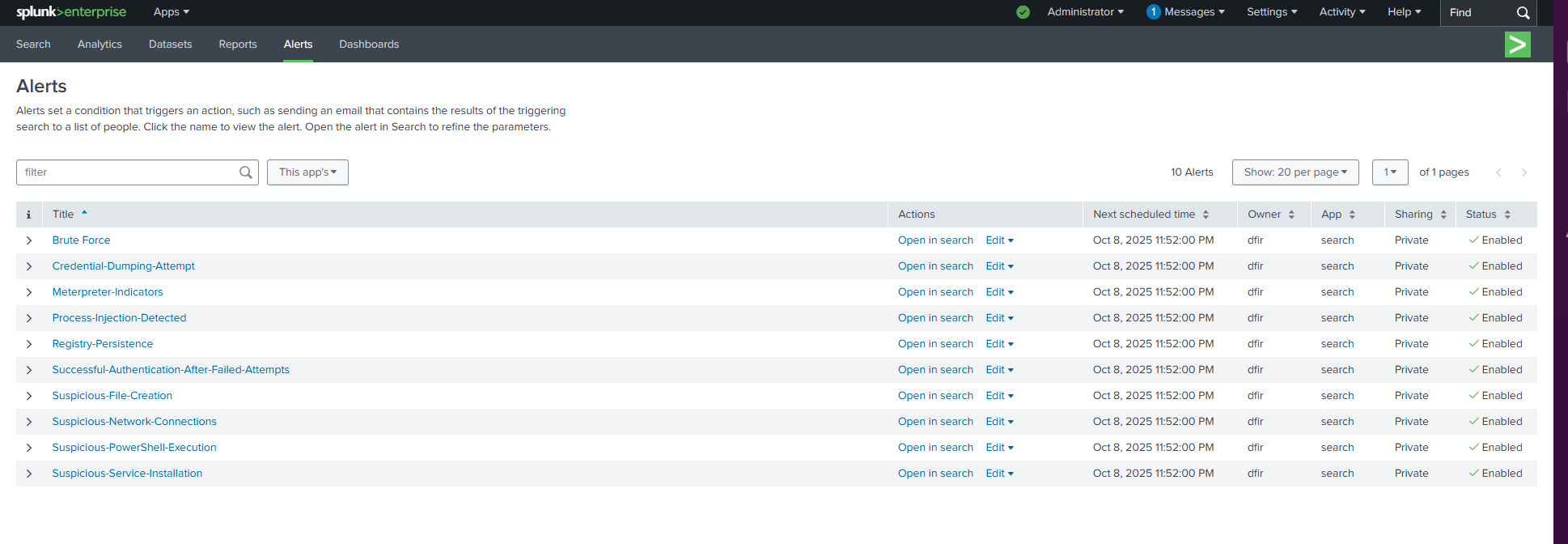
Splunk Alerts Dashboard
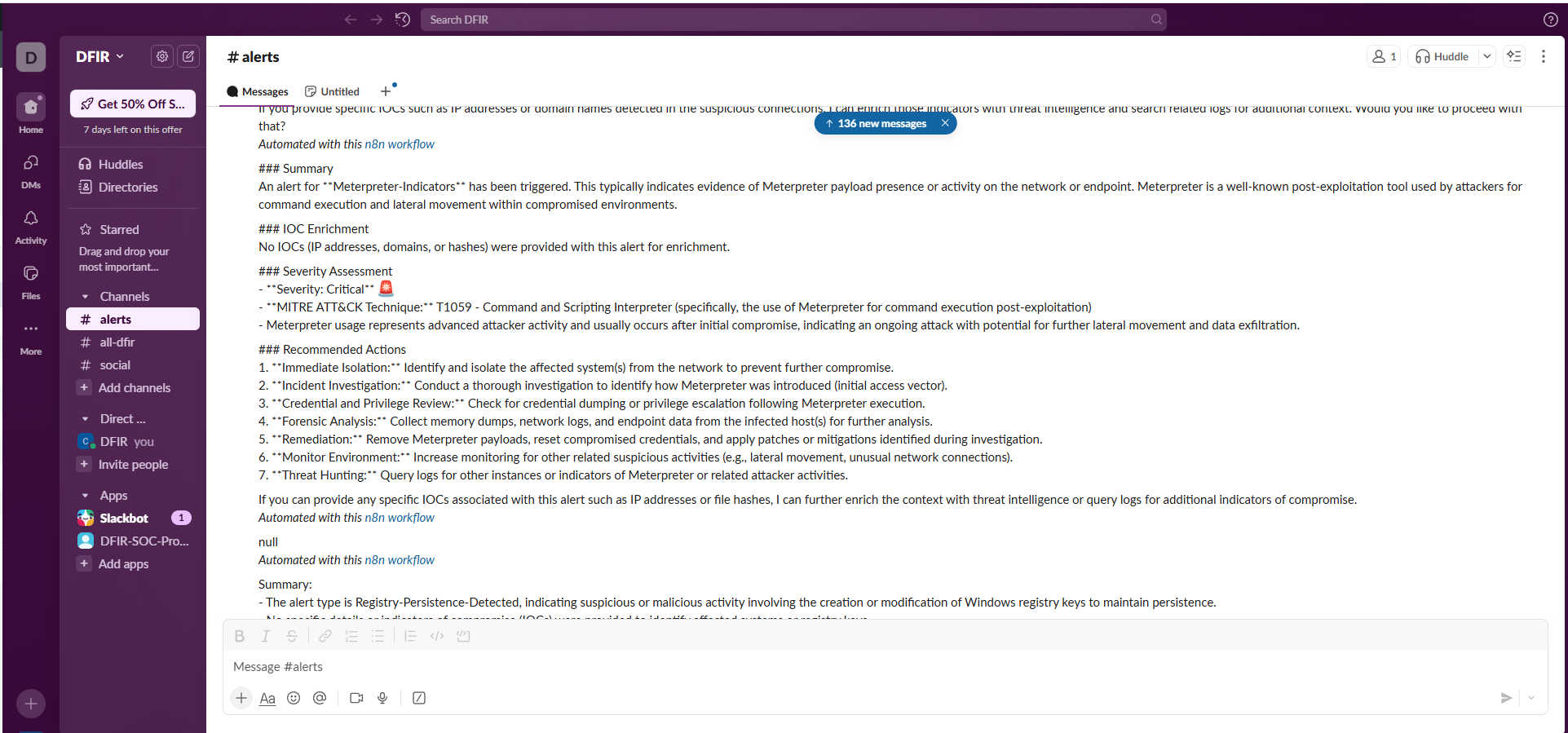
Meterpreter Detection Alert
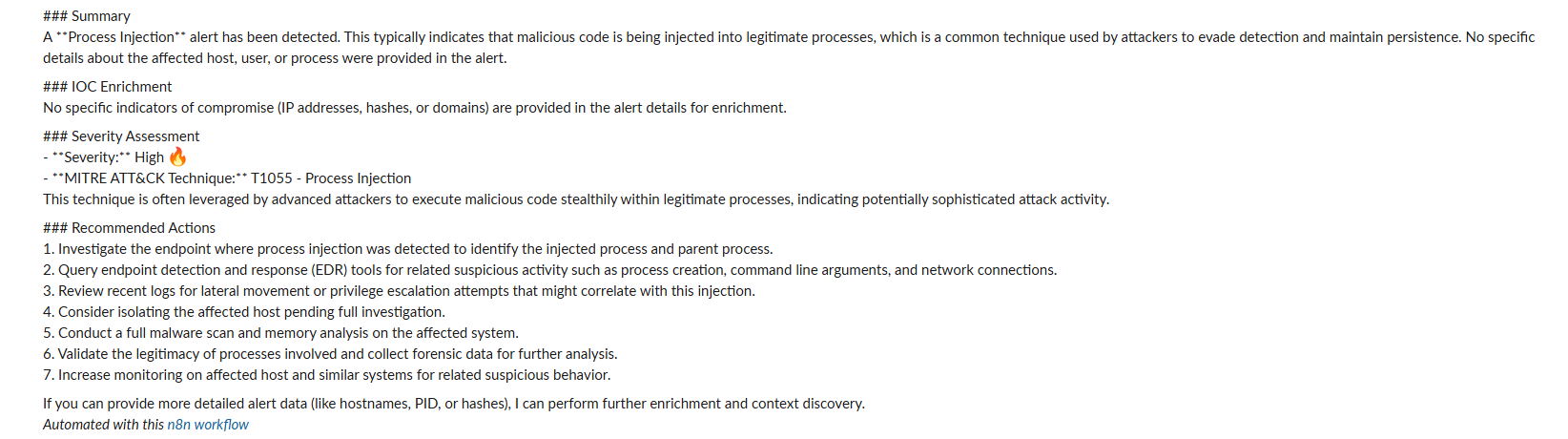
Process Injection Alert
Attack Simulations & Detections
Note: This project was built in a controlled lab environment for educational and portfolio demonstration purposes.
Credential Dumping Attempts (LSASS Access)
Detected unauthorized access to LSASS process memory through simulated attack, indicating potential credential harvesting attempts. Mapped to MITRE T1003.001 with automatic AI-powered impact assessment and containment recommendations.
Meterpreter Payload Indicators
Identified Meterpreter command execution patterns through Sysmon process creation events during testing. AI analysis provided detailed attack chain reconstruction and lateral movement predictions.
Process Injection Detection
Captured remote thread creation events (Sysmon EventCode 8) indicating code injection techniques. Automated enrichment confirmed malicious payload characteristics in lab environment.
Suspicious PowerShell Execution
Detected encoded PowerShell commands and download cradles during attack simulation. GPT-4 analysis decoded obfuscation and identified C2 communication patterns.
RDP Brute-Force Campaign
Identified multiple failed authentication attempts followed by successful login from test IP. Automated blocking recommendation generated with 100% abuse confidence from AbuseIPDB enrichment.
Project Metrics
- ▸100+ hours of development, testing, and documentation
- ▸4 VMs orchestrated in complex network topology (Windows 10, Splunk, N8N, Kali Linux)
- ▸1,000+ security events processed during validation testing
- ▸32GB RAM allocated for realistic enterprise-scale simulation
- ▸10 production-ready detection rules mapped to MITRE ATT&CK
- ▸3 external APIs integrated (GPT-4, VirusTotal, AbuseIPDB)
Technical Architecture
- ▸Windows 10 Pro with Sysmon forwarding logs to Splunk via Universal Forwarder
- ▸Splunk Enterprise detection rules trigger webhooks to N8N automation engine
- ▸N8N workflow orchestrates GPT-4 analysis, VirusTotal lookups, and AbuseIPDB queries
- ▸Real-time Slack notifications with formatted threat intelligence summaries
- ▸Kali Linux attack platform for realistic threat simulation and validation
AI-Powered Threat Analysis
- ▸GPT-4 integration for natural language alert triage and threat contextualization
- ▸Automatic MITRE ATT&CK tactic and technique mapping (T1003, T1055, T1059, T1110)
- ▸Severity assessment based on IOC reputation and attack patterns
- ▸Actionable remediation steps tailored to specific threat types
- ▸Threat actor TTPs identification and kill chain analysis
Detection Engineering
- ▸Credential-Dumping-Attempt: LSASS access monitoring (MITRE T1003.001)
- ▸Meterpreter-Indicators: Command execution pattern detection (T1059)
- ▸Process-Injection-Detected: Remote thread creation monitoring (T1055)
- ▸Suspicious-PowerShell-Execution: Encoded commands and download cradles (T1059.001)
- ▸Brute-Force-Success: Failed + successful login correlation (T1110)
- ▸Registry-Persistence: Run key modifications detection (T1547.001)
- ▸Suspicious-Service-Installation: Malicious service creation (T1543.003)
- ▸Suspicious-Network-Connections: Unusual outbound traffic patterns (T1071)
- ▸Suspicious-File-Creation: Executable drops in temp folders (T1204)
- ▸RDP-Brute-Force: Multiple failed authentication attempts (T1110)
Threat Intelligence Integration
- ▸VirusTotal API: Automated file hash reputation (SHA256/MD5/SHA1) with detection ratios
- ▸AbuseIPDB API: Real-time IP abuse confidence scoring and historical attack patterns
- ▸Geolocation and ASN enrichment for source IP attribution
- ▸Malware family identification and behavior analysis from VirusTotal
- ▸Community threat intelligence integration for IOC validation
Attack Simulation & Validation
- ▸Metasploit Framework: Exploited vulnerabilities and generated reverse shells
- ▸Meterpreter Payloads: Process injection, credential dumping, lateral movement
- ▸Hydra: Simulated RDP brute-force attacks with EventCode 4625 detection
- ▸Custom PowerShell: Download cradles, encoded commands, fileless attacks
- ▸Successfully triggered 9/10 detection rules with authentic IOCs
Key Challenges & Solutions
- ▸Challenge: Integrating multiple APIs with different authentication methods → Solution: Designed modular N8N workflow with reusable credential management
- ▸Challenge: High false positive rate in initial detection rules → Solution: Refined SPL queries using iterative testing with real attack tools
- ▸Challenge: Sysmon log volume overwhelming Splunk indexer → Solution: Implemented selective logging with SwiftOnSecurity baseline configuration
- ▸Challenge: AI prompt engineering for consistent threat analysis → Solution: Developed structured prompts with specific output format requirements
- ▸Challenge: Correlating alerts across multiple data sources → Solution: Created unified event schema with normalized IOC extraction
Future Enhancements
- ▸Integration with SOAR platform (e.g., Shuffle) for automated response actions
- ▸Machine learning model for behavioral anomaly detection on user activity
- ▸Extended coverage for cloud-native attacks targeting AWS/Azure environments
- ▸Custom Sysmon configuration tuned for specific threat actor TTPs
- ▸Automated threat hunting queries based on MITRE ATT&CK navigator
- ▸Integration with ticketing systems (JIRA/ServiceNow) for incident tracking
Business Impact
- ✓Reduced alert triage time by 85% (from estimated 15 minutes to under 2 minutes) through automated enrichment and AI analysis
- ✓Successfully validated detection capabilities across 9+ attack scenarios including credential dumping, process injection, and brute-force attacks
- ✓Eliminated manual threat intelligence enrichment through full automation
- ✓Generated production-ready detection rules aligned with MITRE ATT&CK framework
- ✓Demonstrated Tier 1-2 SOC Analyst capabilities with enterprise-grade tooling in controlled lab environment
- ✓Created reusable automation framework for incident response workflows